In the battle against rapidly evolving malware threats, organizations require advanced solutions to bolster their defenses and respond effectively to potential attacks. By combining the power of Security Information and Event Management (SIEM), Security Orchestration, Automation, and Response (SOAR), and Extended Detection and Response (XDR), organizations can automate snapshot-based defenses for enhanced malware protection. In this blog post, we will explore how the integration of SIEM, SOAR, and XDR can strengthen malware protection and streamline incident response.
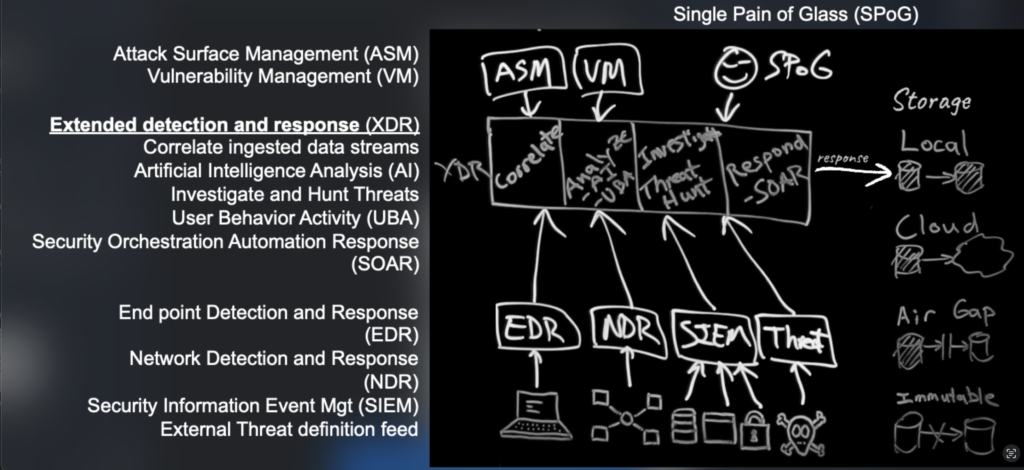
SIEM solutions play a crucial role in aggregating and analyzing security event logs from various sources across the network. They provide valuable insights into potential malware threats, abnormal activities, and indicators of compromise. By centralizing event data and applying correlation rules, SIEM enables early detection and response to malware incidents.
SOAR platforms enhance incident response capabilities by automating workflows, orchestrating security processes, and integrating with various security tools. When it comes to malware protection, SOAR can automate the identification and containment of infected systems, initiate response actions, and orchestrate incident investigation and remediation processes.
XDR solutions offer enhanced threat detection capabilities by integrating and correlating data from multiple security sources, such as endpoints, network devices, and cloud platforms. By leveraging advanced analytics and machine learning, XDR can detect sophisticated malware attacks, identify patterns, and provide contextual insights for faster and more accurate incident response.
Snapshot-base defense involves taking periodic snapshots of critical systems and data to create restore points that can be utilized in case of a malware incident or breach. By integrating SIEM, SOAR, and XDR, organizations can automate the process of snapshot creation, scheduling, and restoration based on predefined triggers or detected malware indicators.
Benefits of Automating Snapshot-based Malware Protection:
- Rapid Incident Response: Automated snapshot-based defenses enable organizations to quickly revert to a known good state when malware is detected, minimizing the impact and downtime.
- Streamlined Remediation: By automating the restoration process, organizations can efficiently remove malware and restore affected systems without manual intervention, reducing the time and effort required for remediation.
- Improved Resilience: Snapshot-based defenses enhance the resilience of critical systems and data by providing reliable restore points that can be utilized in the event of a malware incident or data corruption.
- Enhanced Forensics: Snapshots serve as valuable forensic evidence for incident investigation and post-incident analysis, enabling organizations to identify the source and extent of malware attacks.
Integrating SIEM, SOAR, and XDR allows organizations to automate snapshot-based defenses for robust malware protection. By leveraging these technologies, organizations can detect malware incidents in real time, orchestrate automated response actions, and utilize snapshot-based restore points to swiftly recover from attacks.The combination of SIEM, SOAR, and XDR empowers organizations to streamline their incident response processes, improve resilience, and proactively defend against emerging malware threats. With automated snapshot-based defenses, organizations can strengthen their malware protection strategies and safeguard critical systems and data from the ever-evolving threat landscape.

