Introduction:
In today’s cybersecurity landscape, the need for robust data protection and rapid threat detection is more critical than ever. Cyberattacks are evolving at an alarming rate, with attackers exploiting vulnerabilities and infiltrating networks swiftly. To counter these evolving threats, organizations are turning to advanced solutions that combine real-time anomaly detection on storage arrays with Security Information and Event Management (SIEM) systems. This integration plays a pivotal role in coordinating data protection schemes, such as snapshots and immutable copies, and is gaining significance due to the reduction in dwell time following rapid malware attacks.
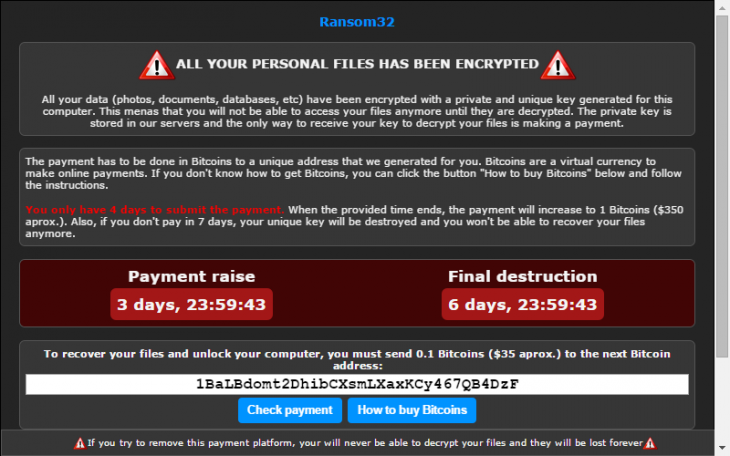
The Swift and Stealthy Threat Landscape:
Cyberattacks have become both swift and stealthy. Attackers are no longer content with lingering undetected for extended periods; they strike quickly and with precision. The reduced dwell time—the duration an attacker goes unnoticed within a network—has shrunk significantly due to the rise of fast-acting malware and ransomware. This shortening dwell time underscores the importance of implementing advanced security measures that can detect and respond to threats promptly.
The Role of Anomaly Detection in Storage Arrays:
Real-time anomaly detection in storage arrays is a game-changer in this context. Here’s why it’s crucial:
- Immediate Threat Identification: Anomaly detection operates at the very core of your storage infrastructure. It scrutinizes data writes in real-time, allowing for the immediate identification of unusual activities or deviations from normal data patterns. This speed is crucial in the face of fast-acting malware.
- Customized Thresholds: For technical professionals, implementing customized anomaly detection thresholds is essential. These thresholds are fine-tuned to your organization’s specific environment, ensuring that anomalies are detected with precision.
- Integration with SIEM: The integration of storage array anomaly detection with a SIEM system is the linchpin of a cohesive defense strategy. The SIEM acts as the central nervous system of your security apparatus, collecting and analyzing data from various sources, including the storage arrays.
The Power of SIEM in Rapid Data Protection:
SIEM systems are essential for technical professionals and security teams. They provide several key functions:
- Correlation and Analysis: SIEMs correlate data from storage arrays with information from other security sources. This technical analysis can identify patterns and anomalies, helping detect and respond to potential security incidents in real-time.
- Automated Incident Response: Technical experts configure automated responses within the SIEM system. When anomalies are detected, these automated responses can include creating snapshots or immutable copies of the affected data. This swift action is critical for safeguarding data from imminent threats.
The Emergence of Cyber Services like Ransomware-as-a-Service (RaaS):
One concerning development in the threat landscape is the emergence of cyber services, such as Ransomware-as-a-Service (RaaS). These services have democratized cyberattacks, allowing even individuals with limited technical skills to become a significant threat.
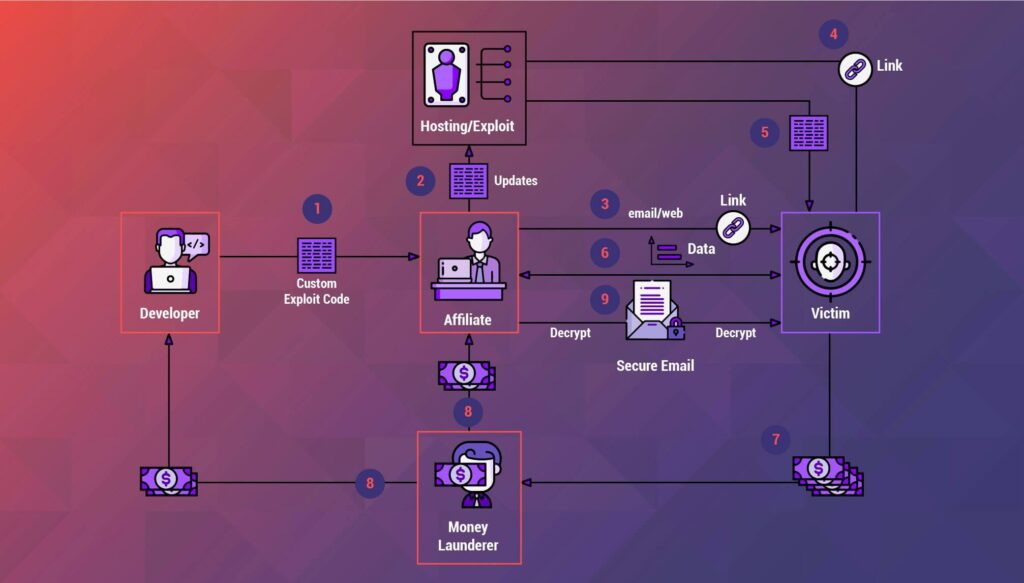
- RaaS Ecosystem: RaaS providers operate as cybercriminal organizations that offer a menu of services to would-be attackers. They provide a ready-made package, including ransomware strains, exploit kits, command-and-control infrastructure, and even support services. Criminal organizations have effectively turned ransomware into a profit-sharing business.
- Low Barrier to Entry: For as little as $150, individuals can access these services and launch attacks. This affordability has transformed ransomware attacks from being the domain of skilled hackers to a threat that virtually anyone can pose.
- Technical Implications: From a technical standpoint, the rise of RaaS underscores the need for rapid detection and response. With attackers acting swiftly and using increasingly sophisticated tactics, organizations must have the technical infrastructure in place to counter these threats.
- Reducing Dwell Time Through Proactive Protection: The reduction in dwell time is a testament to the agility and precision of modern cyberattacks. RaaS offerings make it even more critical to respond promptly. By integrating anomaly detection with data protection schemes, organizations can respond to RaaS-based attacks swiftly and effectively, reducing dwell time and enhancing their cyber resilience.
- Snapshots and Immutable Copies: Technical experts can define rules within the SIEM system to trigger actions like taking snapshots or creating immutable copies of data. Snapshots allow organizations to roll back to clean copies of data, while immutable copies safeguard data against unauthorized alterations.
A Call to Action with IBM’s FlashSystem and QRadar:
To empower your organization with the most advanced tools to combat evolving cyber threats, consider exploring IBM’s FlashSystem and IBM’s QRadar. As leading providers of high-performance storage solutions and SIEM systems, IBM’s FlashSystem and QRadar can seamlessly integrate with your security stack, enhancing the efficiency of anomaly detection and rapid incident response.
- Learn More About IBM’s FlashSystem: Discover how IBM’s FlashSystem can fortify your organization’s cybersecurity defenses. Visit IBM’s FlashSystem for more information.
- Explore IBM’s QRadar: Dive into the capabilities of IBM’s QRadar SIEM system and learn how it can bolster your security operations. Visit IBM QRadar for more details.
Conclusion:
In an era where cyberattacks strike rapidly and stealthily, the integration of real-time anomaly detection in storage arrays with SIEM systems is no longer an option but a necessity. Technical professionals are at the forefront of this transformation, creating custom anomaly detection thresholds, integrating systems, and configuring automated responses. By doing so, organizations are poised to protect their data swiftly and effectively, reducing dwell time and enhancing their cyber resilience in the face of fast-acting malware, ransomware, and the democratization of cyber threats through services like Ransomware-as-a-Service (RaaS).
