In the age of information, our digital footprints are everywhere. Every action we take online leaves traces, and with the right tools, these breadcrumbs can be used to uncover valuable insights. This is where OSINT, or Open Source Intelligence, comes into play. OSINT is the practice of collecting and analyzing publicly available information to make informed decisions.
Publicly available sources, including websites, social media, public records, and more. This information is used to gain a deeper understanding of individuals, organizations, or events. OSINT is invaluable for various purposes, including cybersecurity, threat intelligence, and investigations.

Typical OSINT Sources:
Search Engines: Search engines like Google, Bing, and Yahoo are often the first stop for OSINT. They help in finding publicly available information on the web.
Social Media: Platforms like Facebook, Twitter, Instagram, LinkedIn, and others provide a wealth of personal and organizational data. OSINT analysts often monitor social media for updates and connections.
Public Records: Government databases, court records, property records, and business registries contain valuable information about individuals and organizations.
News Websites: Online news sources and archives can provide historical information and updates about events and entities.
Forums and Message Boards: Niche forums and discussion boards can reveal valuable insights, especially in specific areas of interest.
WHOIS Databases: These databases provide information about domain names, including the owner’s contact details, which can be useful for cybersecurity and investigations.
Shodan: A search engine for internet-connected devices. It helps identify vulnerable or exposed systems and devices.
Wayback Machine: The Internet Archive’s Wayback Machine allows users to view historical snapshots of websites, which can be helpful for tracking changes and historical information.
Online Directories: Websites like Whitepages, Yellowpages, and professional directories provide contact details and information about individuals and businesses.
Dark Web Sources: While not truly open, certain OSINT professionals delve into the dark web to gather information related to cyber threats and criminal activities.
APIs and Data Aggregators: Some services provide APIs and data aggregation platforms that allow OSINT analysts to access multiple sources and perform searches more efficiently.
Government Publications: Government websites often release reports, statistics, and data that can be used for research and analysis.
Academic Publications: Academic journals, research papers, and dissertations can provide authoritative information on various subjects.
Patent and Trademark Databases: These databases contain information on patents and trademarks, which can be valuable for competitive analysis and intellectual property research.
Blogs and Personal Websites: Personal blogs and websites can offer insights into an individual’s thoughts, interests, and activities.
Image and Video Search: Reverse image and video search tools help identify the source and context of images and videos found online.
Job Boards and Professional Networks: Platforms like LinkedIn and job boards can reveal employment history, skills, and professional connections.
Maltego:
A popular open-source intelligence and forensics tool used for data mining and information gathering. It provides a wide range of data sources and transforms that data to help investigators and researchers gather, analyze, and visualize data. The specific data sources available in Maltego can vary depending on the version of the tool and custom transforms that users or organizations may have developed. Here are some common categories of data
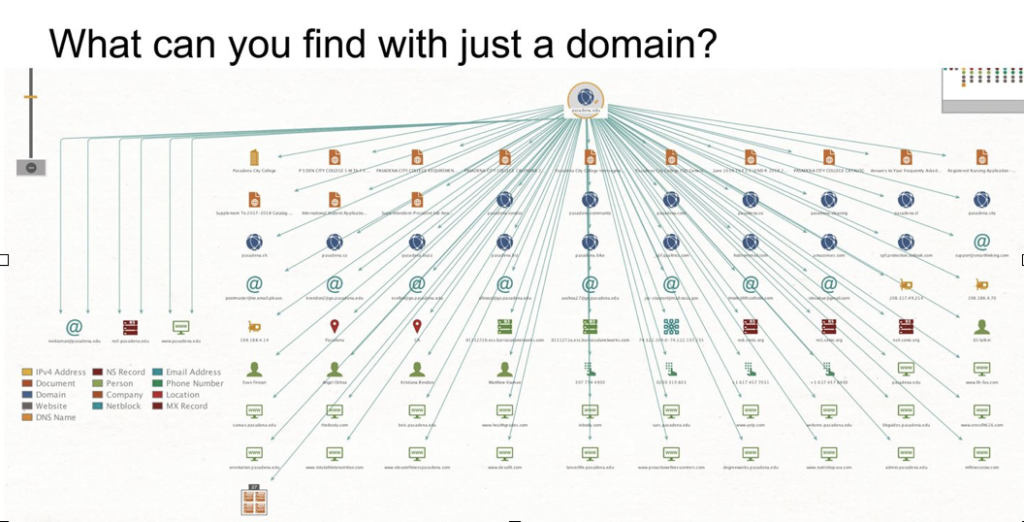
Maltego Data Feeds:
Social media platforms: Maltego can access and retrieve data from social media sites like Twitter, Facebook, LinkedIn, and more.
Domain name registration data: It can extract information about domain names, registrants, and registrars from public databases.
WHOIS databases: Maltego can query WHOIS databases to obtain information about domain ownership.
DNS records: It can gather DNS information, such as IP addresses and hostnames.
GeoIP data: Extracts geolocation data related to IP addresses.
Criminal records: Access criminal databases to gather information on individuals.
Business records: Retrieve data related to companies, including registration details.
Property records: Access land and property records for real estate investigations.
Government records: Access government databases for various purposes, such as searching for individuals or companies.
Publicly available online sources: Maltego can scrape data from websites and forums.
News and media sources: Access news articles and related information.
Research databases: Access academic and research databases for information on individuals, organizations, and publications.
Custom Data Sources: Organizations and individuals can create custom transforms and connectors to access specific data sources not included in the default Maltego set.
API Integrations: Maltego supports API integrations with various data providers and services, allowing users to access a wide range of external data sources. This can include financial data, threat intelligence feeds, and more.
Local Data: Users can import local data files or databases into Maltego for analysis.
Maltego key Features:
Transforms:
Maltego uses transforms to fetch data from different sources and present it in a structured manner. These transforms can reveal connections between entities, such as people, organizations, websites, and more.
Entity Mapping:
Maltego enables the visualization of relationships between entities in a graph format, making it easier to comprehend complex data.
Integration:
It integrates with various data sources and services, allowing users to access a wide array of information from a single platform.
On a recentest engagement using Maltego and a few other utilities I was able to build entity-relationship graphs with data that includes details on domain names, subdomains, email addresses, IP addresses, open ports and services, software versions, potential vulnerabilities, geolocation information, and social media profiles all in under 30 minutes.
Steps to Minimize:
While it’s challenging to completely eliminate all digital traces, these steps can significantly reduce your digital footprint and enhance information security. The key is to maintain a proactive approach to security and privacy, making your company less vulnerable to OSINT threats. By implementing these measures, you’ll be well on your way to protecting your business from unwanted information exposure.
Strong Information Security Policies: Start by creating and enforcing robust information security policies covering data protection, access controls, and employee training. A well-defined strategy is the foundation of your security efforts.
Data Minimization: Collect and retain only the data that’s necessary for your business operations. Regularly review and delete any unnecessary information to reduce your data footprint.
Encryption: Use encryption to protect sensitive data both when it’s at rest and in transit. This safeguards your data from unauthorized access.
Access Control: Implement strong access controls and limit access to sensitive data to authorized personnel. Role-based access controls ensure that employees have the minimum access required for their roles.
Social Engineering Awareness: Train your employees to recognize and respond to social engineering attacks like phishing. Human error is often the weakest link in cybersecurity.
Securing Public-Facing Assets: Protect your websites, servers, and other public-facing assets from reconnaissance and attacks. Regularly update your software and systems with security patches.
Online Presence Monitoring: Regularly monitor your company’s online presence, including social media accounts, websites, and forums. Be vigilant about what information is publicly available and remove any unintended disclosures.
Privacy Settings: Encourage employees to set strict privacy settings on their personal social media accounts. Advise them not to share sensitive work-related information on personal profiles.
Limit Employee Exposure: Minimize the exposure of employee personal information on company websites or directories. Consider using generic contact information for general inquiries.
Legal Protections: Explore the legal protections available for sensitive business data, such as patents, trademarks, and copyrights. Utilize these protections as appropriate to safeguard your intellectual property.
While I spend hours conducting OSINT to uncover potential attack surfaces, tools like Maltego enable me to rapidly gather a wealth of information. Safeguarding your company’s digital footprint is of utmost importance. These steps act as a shield against undesired exposure. By establishing strong security policies, practicing data minimization, employing encryption, and enhancing employee awareness, your business can significantly reduce its vulnerability. Furthermore, proactive measures like monitoring your online presence, configuring privacy controls, and considering legal protections all play essential roles in fortifying your sensitive data. While complete eradication of digital traces is a challenging feat, these collective steps bolster information security, helping your company maintain a competitive edge in the digital landscape.

